General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsAnonymous group allegedly hacked Romney tax records via Franklin firm
Here's the deal though, the article goes on to say that the supposed hackers published a blackmail letter demanding 1 million dollars in return for not releasing the info.
Tuesday, September 4, 2012 at 9:33pm
By Ken Whitehouse
An anonymous individual or group is alleging that they have gained "all available 1040 tax forms" of GOP presidential candidate Mitt Romney by accessing computers in the Franklin office of the professional services firm PricewaterhouseCoopers.
<snip>
"Romney's 1040 tax returns were taken from the PWC office 8/25/2012 by gaining access to the third floor via a gentleman working on the 3rd floor of the building. Once on the 3rd floor, the team moved down the stairs to the 2nd floor and setup shop in an empty office room. During the night, suite 260 was entered, and all available 1040 tax forms for Romney were copied. A package was sent to the PWC on suite 260 with a flash drive containing a copy of the 1040 files, plus copies were sent to the Democratic office in the county and copies were sent to the GOP office in the county at the beginning of the week also containing flash drives with copies of Romney's tax returns before 2010. A scanned signature image for Mitt Romney from the 1040 forms were scanned and included with the packages, taken from earlier 1040 tax forms gathered and stored on the flash drives.
<snip>
A follow up letter was also posted that states:
The deal is quite simple. Convert $1,000,000 USD to Bitcoins (Google if if you need a lesson on what Bitcoin is) using the various markets available out in the world for buying. Transfer the Bitcoins gathered to the Bitcoin address listed below. It does not matter if small amounts or one large amount is transferred, as long as the final value of the Bitcoins is equal to $1,000,000 USD at the time when it is finished. The keys to unlock the data will be purged and what ever is inside the documents will remain a secret forever.
http://nashvillecitypaper.com/content/city-news/anonymous-group-allegedly-hacked-romney-tax-records-franklin-firm
Panasonic
(2,921 posts)NOW!!!!
cynatnite
(31,011 posts)cali
(114,904 posts)disproves this story. I have my doubts too and even if true these people are true sleazeballs, but it seems possible if not probable.
cynatnite
(31,011 posts)We'd also see the networks going insane over this if it were true, too.
It just screams BS to me.
drm604
(16,230 posts)It says they were sent to the Democratic county office. And they were encrypted.
I think it's very likely BS but the story holds up.
cynatnite
(31,011 posts)I still don't buy the story. The variation that appeared on that satirical site I posted is also why I doubt it. Plus I think the media would be scrambling over this.
Also, do you think that the media or political parties can't decrypt it? Do you think they can't get their own hackers just as smart as anonymous? 1 million dollar blackmail? Seriously?
Sorry, I just don't buy this for one second. I'd love for it to be true, but I don't think it is.
If I'm wrong, I will declare it happily and loudly.
EOTE
(13,409 posts)AES is rock solid and there have been extremely few successful attempts to crack it. Do I think they can't get their own hackers just as smart as anonymous? Well, even if they could, it's entirely a moot point. It's far, far, far easier to encrypt data than it is to decrypt it. I'm only moderately educated on decryption/encryption standards, yet I could encrypt data so that 99.999% of the world's most elite hackers couldn't touch it even given several years time.
drm604
(16,230 posts)EOTE
(13,409 posts)The vulnerabilities are such that it still requires a great amount of computing time and power, but it's not 100% fail safe as of now.
http://en.wikipedia.org/wiki/Advanced_Encryption_Standard#Known_attacks
drm604
(16,230 posts)the techniques discussed in that "known attacks" section are simply ways to reduce the needed brute force. They would still take a ridiculous amount of time and resources.
I don't think the side channel attacks are relevant here.
Not that I think there's anything to this story, but I don't know of any show-stopping objections other than the sheer hollywood caper flavor of the whole thing coupled with the total lack of evidence so far.
EOTE
(13,409 posts)As it is, using brute force to crack AES 256 is simply impossible. The computing power and time simply isn't there, even using massive parallel computing. However, using some of these vulnerabilities. the cracking of lesser versions, such as AES 128 are technically feasible given massive amounts of time and resources.
Aerows
(39,961 posts)And being granted access to a local resource? By far the easiest method.
but I doubt that anyone's going to able to talk the key out of whoever did this (in the unlikely case they did actually do it).
Aerows
(39,961 posts)I do. I've seen worse happen. I'd be pleased to privately offer my credentials via PM if you will.
drm604
(16,230 posts)but I don't get your point. Are you saying that someone could use social engineering to decrypt these files (assuming they exist)?
jeff47
(26,549 posts)False.
Brute forcing AES256 is very time-consuming. But not impossible. It's also an almost infinitely-parallelizable problem, so the limitation is the number of machines you use to brute-force it. Also, it's a problem that special hardware can solve much, much faster than a general purpose computer.
For everything you and I could encrypt, nobody's going to bother with the effort. For much more valuable stuff, it's time to break out the soldering irons. It is rumored that the NSA has done so and can now routinely brute-force AES-256 encrypted data. It's obviously difficult to find out if this is actually true or paranoia. But it is within the realm of the possible.
The only unbreakable encryption is one-time pad. Everything else can be broken with enough time and computation.
Aerows
(39,961 posts)or TFlops has rendered brute forcing of some encryption methods trivial. AES-256? No, but with the ability of teraflops of calculations with the parallel processing capabilities of modern graphics cards, not out of reach at all.
EOTE
(13,409 posts)Encryption could be anything from incredibly simple character substitution to AES-256 and beyond. But it's not like AES-256 encryption is terribly difficult to obtain. I think it's going to be quite some time before we see any chinks in its armor. I don't care how powerful these GPUs are, unless you have about 2^30 of them, it's not going to touch AES-256.
EOTE
(13,409 posts)And considering the operations to recover AES-256 encryption is around 2^250+, I don't see that being done anytime in the near future, no matter how much hardware is simultaneously running it. As for the NSA claim, I'd need to see that to believe it. As it is right now, I don't believe we have anywhere near the brute force capability to do such a thing.
jeff47
(26,549 posts)As for rumors, here's one site discussing them - he's skeptical, but doesn't think it's impossible. Feel free to google.
But keep in mind we're not talking about CPU cycles, or even GPU cycles.
We're talking about custom-built chips resembling FPGAs that are built to do the brute force attack a few million times faster than a general purpose CPU. Such devices are theoretical in our world, but people with lots of cash could build them.
It's mathematically possible with a whole lot of such devices to brute force AES-256 in a reasonable time (months if you don't get lucky).
EOTE
(13,409 posts)And a few million times faster wouldn't cut it at all. It would need to be a few trillion, trillion, trillion, trillion times faster if it were to make a dent in AES256. I don't think you understand the absolutely mind boggling numbers we're talking about here. We're talking 2^250 here. That's nothing like the 64^16 or so that's the max that hardware based solutions can run through now. That's many, many, MANY magnitudes of order more. In case you're having a hard time imagining 2^250, imagine a 2 followed by 75 zeros. That's the numbers we're talking about here. That's NOTHING like the toy like encryption that most websites use. It is, for all intents and purposes, uncrackable.
jeff47
(26,549 posts)You're still thinking of this as a single process running on a single desktop computer.
That chip I describe is one chip. You put a few hundred in box. You then get a shitload of those boxes. You use other sources and techniques to reduce the key space. Ta-da! It's now doable.
You'll find that most SSL connections these days use AES for the symmetric encryption.
So your version of the math says it can be done in a very long time, then you declare it impossible.
Pick one.
EOTE
(13,409 posts)Fuck a few hundred, let's have billions of the world fastest supercomputers (the IBM Sequoia) running in parallel. If that were the case, it would only take about a billion years to crack AES256 rather than thousands of trillions of years. Do you understand what type of numbers we're talking about here? I said that for all intents and purposes, it's uncrackable. That is an undeniable truth. It's not impossible, it would just take literally billions of billions of years. Is that clear enough for you? Do you understand how insanely large 2^250 is?
EOTE
(13,409 posts)I suppose nothing is truly impossible. But given current technology, the likelihood of AES256 being broken by brute force is far less likely than monkeys flying out of my ass.
Aerows
(39,961 posts)significantly reduces such time. Just saying.
Not to mention that even if you use a salt, you have to pass it through said algorithm. Do you really think that router authorization devices have been around for 16+ years, and the salt hasn't been partially cracked? Rainbow tables, my friend.
EOTE
(13,409 posts)hours to work properly. I have seen absolutely zero evidence that AES256 has come close to being cracked. I've heard tons of rumors that NSA can do it almost on the fly, but I don't buy that for one second. Until I see at least a smidgen of evidence, I won't believe differently.
And I will assume that you believe 100% that this is an operation to discredit Democrats by making them believe something that they already know to be true due to experience in said industry.
"You are lying, you Democrat, because I fooled you into believing that you are lying" isn't a particularly compelling defense. It smells.
EOTE
(13,409 posts)Because you seem to be reading words that I haven't even come close to writing.
I have no idea whether this is genuine or not, that's not even what I commented on. My initial entering of this OP was to correct some naive notion that if Anonymous was able to encrypt this data that surely there are plenty of people who could decrypt it. That's simply not the case and that's what I was responding to. I'm not exactly sure what it is you're accusing me of, but it's certainly nothing that I've said.
That this isn't necessarily "Anonymous" the group, and is just a bunch of anonymous people. That was my point.
"My initial entering of this OP was to correct some naive notion that if Anonymous was able to encrypt this data that surely there are plenty of people who could decrypt it. That's simply not the case"
I think you need to wait a few days and see if that is the case or not, because you may be proven wrong.
EOTE
(13,409 posts)I never said who this group was or what their motivation is. I simply said that it's VERY easy for people with a modicum of knowledge to encrypt data so that it's effectively uncrackable. Certainly nothing is impossible, but the resources required to crack high level encryption without a key makes it pretty much so.
Aerows
(39,961 posts)Not that you would. Braggadocio has no place in the security field, but some seem to think it is their meat and drink.
EOTE
(13,409 posts)This is your first response to me since you accused me of threatening you. Now you're accusing me of being a braggart? I suggest either laying off on cybercrime novels or perhaps reading a bit more thoroughly before responding in the future.
Aerows
(39,961 posts)I await your magnificent credentials and wide variety of experience with hardware and software to discredit my statements, EOTE.
You are from Maryland, and I assume an Obama supporter, which I respect. But don't assume that with nothing more than insults I will cave on my assessments and experience.
EOTE
(13,409 posts)You accuse me of threatening you when I've done absolutely nothing of the sort.
I've got 17 years in the industry, but that's only because I couldn't start my first real IT job until I turned 16. I guarantee you that I know of which I speak. I said that with today's technology, AES256 is for all intents and purposes impenetrable. That is a fact. You disagreed with that and I asked to hear what made you disagree with my statement. That's when you went on a fairly unbalanced tangent accusing me of threatening you. If that's what you got out of my comment, then you probably need meds. If you DO have anything to contribute that would suggest that what I say is incorrect, please provide it. Otherwise, it just seems like you're posting one paranoid rant after another.
Aerows
(39,961 posts)how it was not impenetrable, particularly using parallel processing GPU's and intelligent algorithms.
That is also fact, and the fact that you evade such usage of technology to paint a picture of incompetence proves that you truly are out of your depth.
In the end, though, this is neither here nor there. Let's wait a few days and see if the hackers got anything of worth before we get egos in an uproar and sling insults like you are doing.
EOTE
(13,409 posts)And several thousand computers running in parallel.
What you're describing is like using a bucket to empty out an ocean rather than a teaspoon. It will save you lots of time, won't it? Sure, you'll empty out the ocean in a few million years rather than a few billion.
What you've presented is not a fact, it's just fairly random information. Do you not think that people have access to all the things that you've mentioned? Do you still not realize that AES256 STILL hasn't been cracked? Do you think that NSA is saying to themselves "Damn, if we'd only thought of that!". You've illustrated nothing of substance.
Aerows
(39,961 posts)Then you are less educated on current hardware and protocols to make use of said hardware.
EOTE
(13,409 posts)All I'm asking you is to provide one little shred of evidence that AES256 has been compromised. You said I was wrong when I said that it hadn't been, so surely you'd be able to provide some information to that extent. But I'm certain that won't happen. Rather, you're going to throw out some buzz terms that you know very little of and say that proves your case. To say you're making an irrational argument would be kind.
Aerows
(39,961 posts)to you, because at this point, you have proven to know nothing of the subject you are attempting to discuss and arguing with you is pointless. I say this with kindness.
EOTE
(13,409 posts)That's somewhat laughable after accusing me of threatening you for asking a simple question.
So now you say you're offering me nothing because I've proven I know nothing of the subject? OK, let's go with that for one minute. So what was your reason for offering me nothing the previous 6 times I asked? Did I know too much then? Listen, I know egos can be fragile things, but honesty is always the best policy. Yeah, you're not offering me anything because I won't understand it. Gotcha chief.
Aerows
(39,961 posts)Let's end this here and now, because it isn't going anywhere good other than bumping this thread. You and I disagree.
EOTE
(13,409 posts)You seem to deal only with your very active imagination. I think the sky is blue, you think it's green, yet you seem utterly incapable of providing even so much as a link (from even the most disreputable source) that says the sky is green. So I'll continue to believe it's blue, thanks.
sir pball
(4,760 posts)As of last year the best public attacks on standard AES were about three orders of magnitude less than brute force. (PDF from MS Research) Still on the order of billion-billions of years on Sequoia for 128, let alone 256. I know that GPUs are insanely fast at embarrassingly parallel jobs like key searches but I haven't heard anything about a 16+ petaflop GPU network anywhere. Not saying a secret machine might not exist, but even so it wouldn't be practically any more useful than the NNSA/ASCP systems - even if it were quite literally a million times faster.
As for these super-duper "intelligent algorithms" you claim knowledge of, you should really give the NSA a call - sounds like something you could make a VERY good living dealing with them on.
EOTE
(13,409 posts)I could provide you my CV, but internet credentials are meaningless anyway. I prefer to deal with actual substance, something that you've been avoiding this conversation. If you have any actual information to suggest that AES256 has even come close to being compromised, you should be able to provide it easily. If you don't, then you're simply being contrary to be contrary.
Aerows
(39,961 posts)by offering scenarios that prove I know my subject. I'm sure you would delight in some pissing match where the junior league engages the senior and somehow proves them wrong, but I don't have time for that, and if you were a true professional, neither would you.
EOTE
(13,409 posts)While providing nothing of substance. Once again I'll ask you, do you have ANY information that suggests that AES256 has even come close to being compromised? If you don't (and it's quite clear that you don't by now), then you're offering up nothing but being contrary for the sake of being contrary. I think what you're demonstrating here is that a little knowledge can be a dangerous thing.
LMAO. ![]() If you thought those were buzzwords...
If you thought those were buzzwords... ![]()
EOTE
(13,409 posts)While having very little idea as to what they mean. If you did know what they mean, you'd know that they offer some assistance in doing what is for now an impossible task. Yes, those things will hasten the ability to decrypt AES256, in that they'd take a job requiring perhaps trillions of computer hours and lessen that to mere hundreds of billions. Either way, it's simply not happening. That you don't recognize that shows how little you know of the subject.
Aerows
(39,961 posts)You have no idea what I am talking about, and that's why you call them "buzzwords" as opposed to fundamental concepts of internet security. If you can teach what you have learned you know it.
EOTE
(13,409 posts)You said I was wrong when I called AES256 uncrackable with current technology. I asked you to provide at least a shred of evidence to support your position. You have been utterly unable to do that. Mentioning current tools used to hasten decryption says absolutely nothing to the fact that AES256 has never been cracked. That's like me saying "It's impossible for anything to travel faster than the speed of light" and you responding "No it's not, rocket boosters!". You see, you need to mention more than simply tools used to accomplish something, you'd need to provide an actual practical application that's been used. If you believe that AES256 has been cracked, surely you should be able to provide some evidence of such. Anyone who could successfully crack AES256 would be hailed as a hero of all heroes amongst the hacking community. BUT IT HAS NEVER HAPPENED. Are you really so dense as to not understand that?
Aerows
(39,961 posts)And I have two of those in my box. Tell me how secure AES256 really is if someone has a much more sophisticated pair of video cards, like 680's or even three of them. Mine is child's play compared to the amount of calculations they can push and they don't use brute force alone but intelligent algorithms that cut the time by x10?
EOTE
(13,409 posts)Do you think these GPU powered password recovery tools could even come close to cracking AES256? Really? So you're able to churn out a few hundred thousand combos per second and you've only got 2^250 to deal with. Awesome!! If you have a few billion years that method is absolutely perfect! You really can't be serious, are you?
On edit: Sorry, make that a few quadrillion years.
If it makes you happy to think AES256 is that solid and secure, you go with it. You win. It is completely solid and cannot be cracked.
And it certainly cannot be cracked under Linux.
Some of us are completely capable of writing and compiling our own, but we bow to this cannot be done instead of wondering, gee, what can I do?
EOTE
(13,409 posts)You could do so with a simple link. Rather, I'm guessing you're more likely to say:
Band saw, sledge hammer, pick axe. See, I told you AES256 can be cracked.
The one link you've provided utterly proves my point for me. Using typical GPGPU decryption to even crack something as simple as 8 character ASCII would take more than a thousand years and AES256 is MANY magnitudes of order more complex. What about this don't you understand?
Sorry, I've had enough of banging my head against the wall for one night.
Aerows
(39,961 posts)of banging your head against the wall trying to convince a person that knows better that they don't.
I don't think you particularly understand low level programming, particularly low level GPU programming as well as you think you do. Visit www.beyond3d.com You will find people that excel at hardware programming as well as utilizing software at an abstraction layer, but mostly, you will learn that when you can program at a hardware level, things are extremely efficient.
http://forum.beyond3d.com/showthread.php?t=62286
EOTE
(13,409 posts)It will require some high school math, so pay attention.
First of all, thanks for providing that link because it just reenforces what I've been saying from the get go, which is that cracking AES256 is utterly impossible using current technology.
Now, if you had read your own article that you so thoughtfully provided, you'd see that the type of passwords they're cracking there are typically 8 characters with about 64 (6 bit) unique possible characters per slot. 8 characters might be on the low side for this hardware/software, so let's take the absolute most rosy scenario that this article provides and let's say that 16 character passwords are routinely cracked by this (it's not at all, but let's pretend). So, that would mean that in order to crack such a password, you'd need to go through around 64^16 (or 2^96) possible permutations. Now, that's a staggeringly high number indeed, but it's insanely, microscopically tiny compared to the amount of permutations required to crack an AES256 key. AES256 on the other hand has ~2^250 permutations required to crack. Do you know how much larger the second number is compared to the first? It's around a trillion, trillion, trillion, trillion times larger. That's a very big number, isn't it? To better illustrate this, take a look at the chart that you so kindly provided in your article:
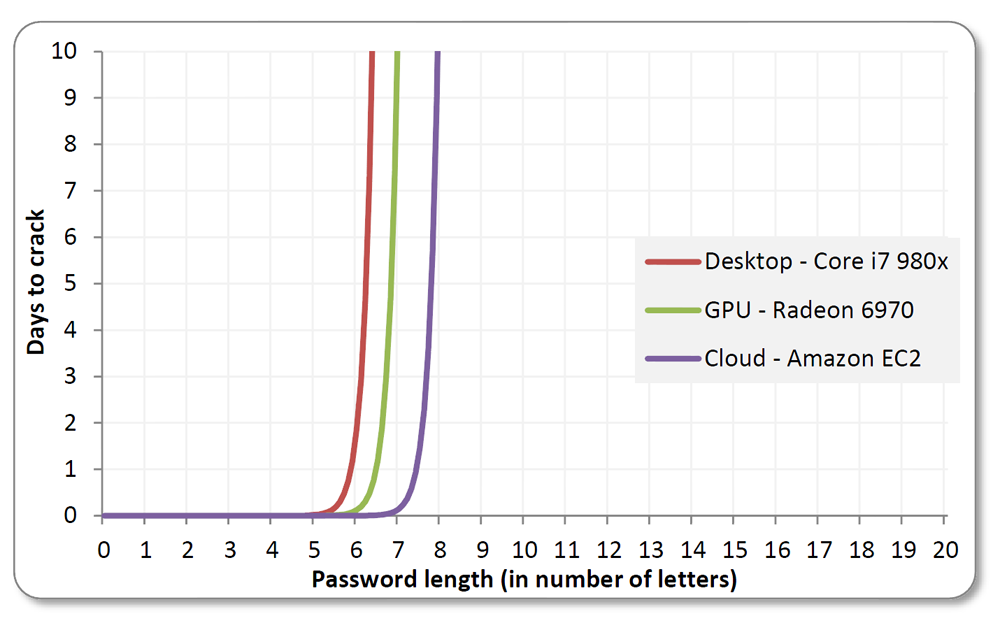
This is what's called the "exponential wall of brute force cracking". Do you see how ungodly steep those curves are? Do you see how even using the Amazon EC2 with the combined power of 1000 powerful GPUs that after 8 characters the time involved becomes astronomically high? Now, you can only see a small fraction of the time curve because it becomes unwieldy very quickly. After 14 characters, you're talking years if not more, even using the EC2. After that, we're talking decades, centuries and millenia. AES256 encryption uses the equivalent of around 32 8-bit characters. Even assuming that these characters are words that are typically used, things like rainbow tables and massively parallel GPU computing would only make a tiny, tiny dent in the amount of time required to crack such a thing. You need to not only familiarize yourself with what's going on with the hardware and software here, but you really need to familiarize yourself with the scope of the numbers we're dealing with. AES256 is nothing like the toy-like encryption these websites use, NOTHING. Until you're able to even have the slightest grasp of the numbers we're dealing with, you're not going to understand why this is impossible. Now go on and explain to me how REAL modern technology is several trillion, trillion, trillion times more powerful than the article you provided says.
snooper2
(30,151 posts)Some engineers at Microsoft figured out a theoretical way to crack AES 3 to 5 times faster, but it would still take a couple billion years ![]()
IDG News Service - Researchers from Microsoft and Belgian Katholieke Universiteit Leuven have discovered a way to break the widely used Advanced Encryption Standard (AES), the encryption algorithm used to secure most all online transactions and wireless communications.
Their attack can recover an AES secret key from three to five times faster than previously thought possible, reported the Katholieke Universiteit Leuven, a research university based in Belgium.
The researchers caution that the attack is complex is nature, and so can not be easily carried out using existing technologies. In practice, the methodology used by the researchers would take billions of years of computer time to break the AES algorithm, they noted.
But the work, the result of a long-term cryptanalysis project, could be the first chink in the armor of the AES standard, previously considered unbreakable. When an encryption standard is evaluated for vital jobs such as securing financial transactions, security experts judge the algorithm's ability to withstand even the most extreme attacks. Today's seemingly secure encryption method could be more easily broken by tomorrow's faster computers, or by new techniques in number crunching.
http://www.computerworld.com/s/article/9219297/AES_proved_vulnerable_by_Microsoft_researchers
snooper2
(30,151 posts)How secure is AES against brute force attacks?
Mohit Arora, Sr. Systems Engineer & Security Architect, Freescale Semiconductor
5/7/2012 1:29 PM EDT
In the world of embedded and computer security, one of the often debated topics is whether 128-bit symmetric key, used for AES (Advanced Encryption Standard) is computationally secure against brute-force attack. Governments and businesses place a great deal of faith in the belief that AES is so secure that its security key can never be broken, despite some of the inherent flaws in AES.
This article describes the strength of the cryptographic system against brute force attacks with different key sizes and the time it takes to successfully mount a brute force attack factoring future advancements in processing speeds.
Any cryptographic algorithm requires multi-bit key to encrypt the data as shown in Figure 1.


As shown, it will take a maximum 16 rounds to check every possible key combination starting with "0000." Given sufficient time, a brute force attack is capable of cracking any known algorithm.
The following table just shows the possible number of key combinations with respect to key size:

Figure 4: Time to crack Cryptographic Key versus Key size
Faster supercomputer (as per Wikipedia): 10.51 Pentaflops = 10.51 x 1015 Flops [Flops = Floating point operations per second]
No. of Flops required per combination check: 1000 (very optimistic but just assume for now)
No. of combination checks per second = (10.51 x 1015) / 1000 = 10.51 x 1012
No. of seconds in one Year = 365 x 24 x 60 x 60 = 31536000
No. of Years to crack AES with 128-bit Key = (3.4 x 1038) / [(10.51 x 1012) x 31536000]
= (0.323 x 1026)/31536000
= 1.02 x 1018
= 1 billion billion years

As shown above, even with a supercomputer, it would take 1 billion billion years to crack the 128-bit AES key using brute force attack. This is more than the age of the universe (13.75 billion years). If one were to assume that a computing system existed that could recover a DES key in a second, it would still take that same machine approximately 149 trillion years to crack a 128-bit AES key.
EOTE
(13,409 posts)Please tell me more about your efficient algorithms which are trillions upon trillions of times more efficient than ones currently known. You're really going to disparage my knowledge? Really? I was willing to believe that you were truly qualified before this conversation began (if extremely misinformed on this subject). But you've proven how extremely little you know about this subject. You belong nowhere near anything security related.
snooper2
(30,151 posts)There's an "engineer" at my work across the street in telecom for 30+ years and he is still a fucking idiot LOL
My question is how come all these big customers ask about TLS all the time with one of our VoIP products but never actually order it ![]()
EOTE
(13,409 posts)Sequoia simply isn't trying hard enough if it can't crack AES256 in less than a trillion years. I think if it was really trying and had the proper motivation, it could do it in a few hours. You're simply not thinking like someone with more than two decades in the business.
snooper2
(30,151 posts)but that would involve waterboarding and some other actions I can't mention here to the person who actually knew the passcode ![]()
sir pball
(4,760 posts)AES *has* been "broken"...but "[f]or cryptographers, a cryptographic "break" is anything faster than a brute force—performing one trial decryption for each key (see Cryptanalysis)." - teh wikiz
The best known attack against the weakest version of standard-compliant 128-bit AES (there are faster attacks, but they're against ciphers with below-specified rounds) has a computational complexity of 2^126.1 (1) - using 100% of the capacity of the world's fastest supercomputer, at a ridiculously optimistic 1000 operations per check, would take 3.6 TRILLION years. Just for poops and giggles, the best AES-256 (which AFAIK is pretty much the only version utilities use anymore) attack is 2^254.4, for a runtime of....wait for it...37.6 billion trillion years!
Incidentally, those numbers are what makes me kind of think this might NOT be a hoax - the public at large would believe that records can be "hacked" off of the IRS or PwC's systems, but I'd wager a year's pay all that data is quite well encrypted; barring a leak of the keys, there's zero chance of getting the data off the servers. Physical access to paper records is far far more plausible in the real world.
cynatnite
(31,011 posts)EOTE
(13,409 posts)A person with a 60 IQ could use a number of modern encryption formats and have their data be damned near 100% safe if the decrypters lack the decryption key. This has nothing to do with how smart the people are.
cynatnite
(31,011 posts)I don't believe anything is impenetrable.
As I said earlier, if this story turns out to be true I will happily and loudly apologize.
EOTE
(13,409 posts)And that's with most likely millions of man hours attempting to crack it. So yeah, I don't think that anyone has anything to worry about if they've encrypted using a modern encryption standard. Sure, AES 256 isn't impenetrable, just impenetrable given the technology that we'll have for the next several decades.
Aerows
(39,961 posts)as a serious threat. Not that I am a hacker, just stating reality.
EOTE
(13,409 posts)I assume you can tell me of AES256 being compromised in an even semi-effective manner? Go ahead, I'm listening. I don't buy it for a second now, but my mind is opened if you happen to have any evidence to sway me.
Aerows
(39,961 posts)And thought to voice it...
Go fuck yourself. There are plenty of people that understand security and work in security and are not intimidated by some person coming along saying "Oh, you must be a traitor if you understand this technology".
EOTE
(13,409 posts)I threatened you? Just how exactly? I asked if you could tell me specifically why you believe that AES256 had been compromised. If you took that as a threat, that's your problem, not mine. Go fuck myself? Because I asked a question? I think you need some help.
I understand security fine, thanks. That's part of my job.
Aerows
(39,961 posts)ever utilized rainbow tables to discover the salt. Not ever.
sir pball
(4,760 posts)Salt is specifically a defense against rainbow tables. Your statement is completely nonsensical; thirty seconds with Google and teh Wiki would have at least given you the information to say "Not that anyone ever discovered the salt and then used a rainbow table".
http://en.wikipedia.org/wiki/Salt_(cryptography)
http://en.wikipedia.org/wiki/Rainbow_table
http://www.codinghorror.com/blog/2007/09/rainbow-hash-cracking.html
http://www.healthypasswords.com/content.What_are_hashes_and_Rainbow_Tables.html
sabrina 1
(62,325 posts)asking for ransom for material like this are criminals. Sounds like extortion to me, rather than providing the public with information. If anyone were to pay them for that info, they would be engaging in a crime also. Sounds like a weak attempt to entrap Democrats into engaging in criminal activity. I am sure they are smarter than that.
This is not the MO of Anonymous.
Aerows
(39,961 posts)Some people socially engineered getting Romney's tax returns, said they were going to release them on Sept. 28, and let the firestorm ensue. Anonymous MO
The second post was that they demanded money, but no one so far has come forward demanding money except for post No. 2, which wants Bitcoins regulated (reportedly). Not Anonymous MO.
Republicans are pissing in their pants at this point.
bemildred
(90,061 posts)I can over here from Meta for the geek war.
I have degrees in Math (BA) and Computer Science (MS) and encryption was one of my hobbies.
I think you have the right of it, with the exception (theoretically) of 100%.
Anybody that does crypto professionally, feel free to correct me as needed.
The only theoretically uncrackable code is the one-time pad, last time I heard. All the mathematical encryption methods are all based on computations that are "easy" with the key (one or more of the terms of the computation) and infeasible without it. "Infeasible" means theoretically possible with known and usually "easy" algorithms, but of very high computational order, i.e. you will never finish unless the problem is very small. The usual thing is based on factorization of very large composite integers.
AES is considered "weak" and is out of fashion, though I quite agree it is good enough for most purposes, and yet I would not bet on it being invulnerable to the spooks. But the various free encryption packages out there now I would expect could be made good enough even for that, I don't know that, but that is how I would bet.
In ALL of the mathematical methods, it is EASY to make the problem bigger, if AES256 is cracked, you can go to AES512 or AES1024 and so on, so while it is theoretically feasible to crack these methods (not 100% uncrackable) it is also theoreticaly very easy to make the problem much much harder when that happens, if you care to.
There are about a gazillion encryption methods out there now, it's a very active field.
Edit: nothing more to add.
drm604
(16,230 posts)I think this story is likely BS, but unbreakable encryption DOES exist and anyone, you and I included, can make use of it with freely downloadable software. My degree is in computer science and I know what I'm talking about. Breaking it is not a matter of hacking. Reality is not like the movies.
Aerows
(39,961 posts)But I have 22+ years experience. Algorithms, salts and parallel processing.
drm604
(16,230 posts)then our financial system would have collapsed by now due to all of the successful attacks against electronic money transfers. That doesn't seem to have happened.
drm604
(16,230 posts)but that satire story is completely different from the one in the OP.
FreeState
(10,584 posts)In one we have them getting the tax records from the accounting firm and the other they broke into the IRS. Not the same story.
leveymg
(36,418 posts)I wouldn't give much credence to this - if you're going to blackmail, why send it to the Democrats without anyone even paying for it first?
The sulphurous smell of the ghost of Rove is still in the room.
drm604
(16,230 posts)the drives they've sent out are encrypted and they're threatening to release the key if they're not paid (or if they are paid by Romney's opposition). Presumably the one sent to PWC is unencrypted as proof that they actually have the data (since they stole if from PWC to start with, sending it to them reveals nothing).
I'm skeptical of the story, but I guess we'll see how it plays out.
drm604
(16,230 posts)Actually, I'm skeptical. It'll be interesting to see how this plays out.
They could easily be full of crap but hoping that someone will pay anyway. I assume, if this is for real, that the drive they sent to PWC is unencrypted so that this can be verified. The Romney campaign is probably already in contact with PWC to see if there's any truth to this.
gollygee
(22,336 posts)even if it isn't true. The idea that we could have a president so open to blackmail is a bit scary.
Aerows
(39,961 posts)But first, we have to find out if this is real or not. I hope PWC got an unencrypted version to verify that it is true.
DonRedwood
(4,359 posts)flamingdem
(39,325 posts)poor mitt is a victim!
Hutzpa
(11,461 posts)They're not a serious group. They're full of shit.
Aerows
(39,961 posts)They are claiming to have references that only PWC would have so that they would know it isn't a fake.
Spirochete
(5,264 posts)Just go arrest Dr. Evil - problem solved.

Aerows
(39,961 posts)Notice at the bottom it says "References to avoid fakes that only you would have."
So, this could be true if they actually included some things that only PWC would know!
drm604
(16,230 posts)The article says that a copy was sent to PWC but I don't see any mention of that in the actual document.
I wonder what their source is?
nc4bo
(17,651 posts)On a sidenote: Just the idea that something like this may (but probably did not) happen is absolutely delicious. ![]()
nc4bo
(17,651 posts)Now if such reports were indeed made?.............oh dear.
Hutzpa
(11,461 posts)according to the article, they gained access from the third floor by asking a fine gentleman to let them in and then
proceed to the second floor where the company is located, unless I'm mistaken, but that's from the article.
nc4bo
(17,651 posts)Unless these people were so careful that they left everything exactly the way they found it.
Correcting because they mentioned the flash drives..............there will be a digital record on whatever machine they used to access the records. I'm positive of that.
![]()
cthulu2016
(10,960 posts)"the Democratic office in the county"
Written by someone with a poor sense of American politics... tonally reminiscent of Nigerian Treasury Minister email scams.
A distasteful hoax.
reformist2
(9,841 posts)Or at least give him nightmares. LOL
HooptieWagon
(17,064 posts)I would think Romney would pay far more to prevent his returns being released. Makes me think the story is a hoax.
cthulu2016
(10,960 posts)DefenseLawyer
(11,101 posts)
bullwinkle428
(20,630 posts)Major Hogwash
(17,656 posts)Hahaha!!!
No shit!
![]()
valerief
(53,235 posts)drm604
(16,230 posts)but maybe larger amounts just wouldn't work?
nebenaube
(3,496 posts)Plus, bitcoin addresses are disposable and fairly anonymous. It could be a scam to drive the value of bitcoins up but that's due to happen soon anyway.
Aerows
(39,961 posts)There's a hard limit of no more than 21 million Bitcoins to prevent devaluation.
http://en.wikipedia.org/wiki/Bitcoin
former9thward
(32,082 posts)cynatnite
(31,011 posts)drm604
(16,230 posts)cali
(114,904 posts)it's outside the realm of possibility.
Aerows
(39,961 posts)"The nice gentleman that let us in" is the most effective hack security has. Whether that includes hacks, manipulation, or just plain smooth-talking, it has always been easier than trying to crack security.
Aerows
(39,961 posts)Social engineering is by far more effective in obtaining information than "hacking". Look at HB Gary - they got the passwords they needed for the whole outfit by a young woman calling on the phone. And the fact that the dude was so stupid he used his own first initial and last name as a login. LOL.
berni_mccoy
(23,018 posts)It's that simple. They need to prove you have the goods without causing the damage they threaten.
Aerows
(39,961 posts)They have provided references to distinguish what they have from fakes.
Skidmore
(37,364 posts)Aerows
(39,961 posts)It very well could be, I'm just interested to hear your take on it ![]()
Skidmore
(37,364 posts)were responsible for somehow injuring his candidate. Rove is a filthy little critter without any sense of ethics whatsoever. Here's a tick list for your reference.
http://www.seattlepi.com/local/opinion/article/Rove-s-dirty-tricks-Let-us-count-the-ways-1246665.php
Lone_Star_Dem
(28,158 posts)I'm bookmarking it. Thanks! ![]()
Lone_Star_Dem
(28,158 posts)Note how they say they got "all available 1040's"
Linking the theft to the Dem party in people's minds = bad for the Democrats.
The returns they stole having no controversial information in them = good for the the Republicans.
Also, Rove's pulled stunts like this before.
In 1986, Rove helped Clements become governor a second time. In a strategy memo Rove wrote for his client prior to the race, now among Clements's papers in the Texas A&M University library, Rove quoted Napoleon: "The whole art of war consists in a well-reasoned and extremely circumspect defensive, followed by rapid and audacious attack."
In 1986, just before a crucial debate in campaign, Rove claimed that his office had been bugged by Democrats. The police and FBI investigated and discovered that the bug's battery was so small that it needed to be changed every few hours, and the investigation was dropped. Critics, including other Republican operatives, suspected Rove had bugged his own office to garner sympathy votes in the close governor's race.
http://en.wikipedia.org/wiki/Karl_Rove
I'm smelling GOP lies and distraction, too.
Aerows
(39,961 posts)Just pointing out that social engineering is the most useful tool in a hackers box. It's one Karl Rove, uses, too. We won't know until something more happens with this story.
Lone_Star_Dem
(28,158 posts)I'm thinking wacky (Paulite?) hoax now. Not that they claim to have done it, I'm sure someone is making such a claim. I'm kind of doubting they have anything though.
Lars39
(26,116 posts)It's the 17th richest county in the US and is hardcore red.
Lex
(34,108 posts)It's a weakness.
I'd love to be a fly on someone's wall right about now.
woodsprite
(11,926 posts)They probably thought asking for a mil would be less likely to smell like an orchestrated stunt.
in the original posting they didn't ask for money. They just said it was going to be release on 9/28. I think the second post is the one Rove cooked up to discredit that maybe, just maybe, they are running scared and actually do have information. They did say that they had references.
drm604
(16,230 posts)This is the first I've heard of any of this.
"PWC Office @ 830 Crescent Centre Drive, Suite 260, Franklin, TN 37067
Telephone: [1] (615) 503-2860
Romney's 1040 tax returns were taken from the PWC office 8/25/2012 by gaining access to the third floor via a gentleman working on the 3rd floor of the building. Once on the 3rd floor, the team moved down the stairs to the 2nd floor and setup shop in an empty office room. During the night, suite 260 was entered, and all available 1040 tax forms for Romney were copied. A package was sent to the PWC on suite 260 with a flash drive containing a copy of the 1040 files, plus copies were sent to the Democratic office in the county and copies were sent to the GOP office in the county at the beginning of the week also containing flash drives with copies of Romney's tax returns before 2010. A scanned signature image for Mitt Romney from the 1040 forms were scanned and included with the packages, taken from earlier 1040 tax forms gathered and stored on the flash drives.
The group will release all available files to the public on the 28 of September, 2012
This line is on all the package letters for authenticity of the email being sent.
all these considerations did not deter me from the path of duty"
here is the post:
http://pastebin.com/zdU1TK40
Take it for what it is worth.
silverweb
(16,402 posts)[font color="green" face="Verdana"]They physically gained access, photocopied and scanned the paperwork, and stored it on flashdrives. That's not "hacking" in any sense and the "anonymous group" is NOT Anonymous.
If it even happened at all, regarding which I have my doubts.
BeHereNow
(17,162 posts)We are so on to your malicious machinations.
You really need to come up with some new tricks.
BHN
Aerows
(39,961 posts)There were two. The first didn't demand money. I just outlined that they were going to release them. The second is a bid for sympathy by making Romney look like a victim.
Laura PourMeADrink
(42,770 posts)to get their hands on some of this and make a chunk...but I was thinking more on the lines of
selling it to a newspaper/TV channel
former9thward
(32,082 posts)This is a silly internet hoax.
NotThisTime
(3,657 posts)drm604
(16,230 posts)but I would think that we would have heard something from one of the major news outlets they supposedly sent encrypted disks to, unless they haven't sent them yet.
BitCoins doesn't seem like the best way to launder that much money. Yes, there is a cash market for buying and selling, but I'd think that it would be difficult to buy that much at once without driving the price up. Selling that much would also seem to be difficult and would drive the price down.
Maybe this is an attempt to manipulate the Bitcoin market.
Aerows
(39,961 posts)guns and drugs. So it isn't outside of the realm to have it happen to drive up the value of Bitcoin currency.
I would think that this is a hit piece on Bitcoin so that they can be treated like money launderers.
I admit that, but I wonder why you think that this is any different than anyone else that ever established a currency standard, including PayPal. PayPal was accused of this very thing.
drm604
(16,230 posts)I don't really have any opinion on Bitcoin at all. I just think this may be a stunt to manipulate the Bitcoin market.
Hell, maybe they posted those two Bitcoin account numbers hoping that a bunch of stupid Romney and Obama supporters would flood them with Bitcoins.
Aerows
(39,961 posts)I was speaking rhetorically.
drm604
(16,230 posts)Aerows
(39,961 posts)I guess it could happen.
drm604
(16,230 posts)Aerows
(39,961 posts)I wonder what is actually on them.
NYC Liberal
(20,136 posts)It's either stolen or it's fake and possibly a setup. Nothing good could come out of it.
Coyotl
(15,262 posts)This could be a rogue pretending to be a criminal because you usually don't splash your crime all over the media
Comrade_McKenzie
(2,526 posts)Just release the damn information and enjoy the fallout.
cbdo2007
(9,213 posts)freshwest
(53,661 posts)“Court Ruled That Media Can Legally Lie” - The Steve Wilson/Jane Akre case v. Fox
http://www.democraticunderground.com/discuss/duboard.php?az=view_all&address=389x6621412
As much as I'd like to smite Mittens, this would never hold up in a court of law, much less in the court of public opinion.
If the Democrats don't denounce it, this will be painted as our own Watergate break-in. That ball and chain belongs to our opposition, not us.